The Information Security Management System monitors and coordinates information security efforts.
Objective
The goal of the information security efforts at Umeå University is to protect our information assets against relevant threats and risks and to maintain information security even if undesirable events occur, such as disruptions, incidents or crises. We want to create effective management through appropriate procedures and balanced security measures to ensure that we protect systems and information regarding the security aspects of confidentiality, availability and accuracy.
Management system for information security
Activities in the management system.
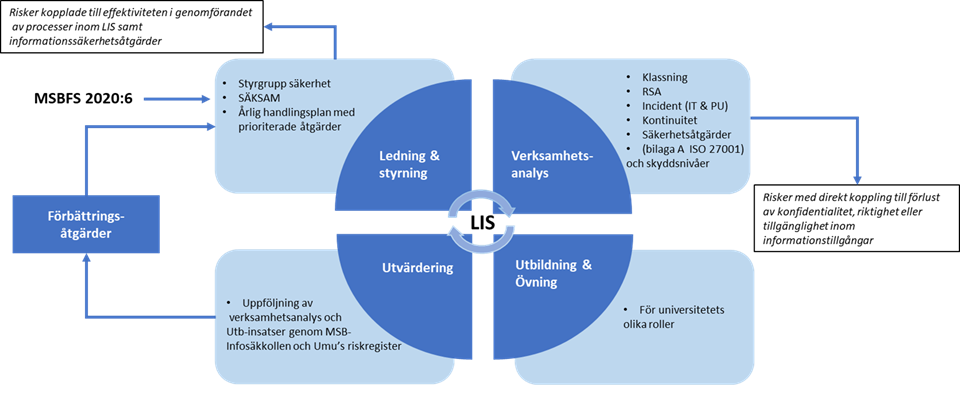
Management and governance
Annually analyse current legislation and regulations and plan the next year's priorities for information security. This includes prioritising identified improvement measures and preparing an annual review with University Management.
Operations analysis
Activities for actual information security. The starting point is the information classification and the risk and vulnerability analysis, which determines technical and organisational security measures based on the respective results.
Incident management is conducted according to an established process and includes IT security incidents and personal data breaches.
System and information owners of IT systems and services that manage mission-critical information assets are to enact plans that enable them to continue operating the system at a reasonable level if it experiences any kind of disruption. (Continuity planning)
Training and practice
All employees are encouraged to undergo basic information security training and to update their knowledge about information security on an ongoing basis.
Different roles within the University also undergo training and receive information based on specific needs. For example, through workshops on information classification and risk and vulnerability analyses and training for new employees and new managers.
Plans for ensuring continued operation in the event of disturbances are to be practiced on a regular basis.
Evaluation
Follow-up of operational analysis and training activities through the Swedish Civil Contingencies Agency's Infossäkkollen tool and Umeå University's risk register.
The University conducts risk and vulnerability analysis of systematic information security. The risk and vulnerability analysis presents different types of possible risks:
- risks that pertain to achieving the intended results of the information security management system as a whole;
- information security and personal data risks related to loss of confidentiality, accuracy and availability of our data processing operations, how likely they are to occur and what consequences this may have on activities, operations and the organisation.
Roles and responsibilities
University Board and Vice-Chancellor
The University Board and the Vice-Chancellor have overall responsibility and the Vice-Chancellor appoints the Information Security Officer.
Information Security Officer
The Information Security Officer is the University Director or the person or persons delegated to serve in this role. This person is responsible for planning, coordinating, following up and monitoring compliance with the University's work on information security.
Dean, head of department or head of unit
The dean, head of department or head of unit is responsible for planning, coordinating, following up and monitoring compliance with information security in their faculty, department, centre or unit.
Information owners
Each information asset is to have an information owner. The information owner is responsible for the confidentiality, availability and accuracy of the information asset. The information owner can be a head of research, a head of department or head of an area.